Multi-tenant user management in Microsoft Teams is one of the most overlooked but critical challenges facing IT teams in modern enterprise environments. As organizations adopt Microsoft 365 across distributed teams, subsidiaries, acquisitions, and regulatory boundaries, managing users across multiple tenants becomes more than an administrative hurdle—it quickly becomes a strategic concern. Inconsistent provisioning, manual processes, and fragmented policies not only waste time—they also introduce compliance risks, inflate license costs, and degrade the user experience.
This guide explores ten in-depth best practices for streamlining user management across multiple Microsoft Teams tenants. Each one addresses real-world problems IT admins face and offers proven, scalable approaches for creating consistency, improving governance, and reducing operational overhead.
For a complete overview of what Microsoft Teams multi-tenant management involves, read our full admin guide here: https://callroute.com/tech-blog/how-to-manage-microsoft-teams-multi-tenant-environments/
1. Create a Unified Provisioning Framework Across Tenants
Provisioning is the first critical step in ensuring users can be productive with Microsoft Teams. In a single-tenant environment, onboarding might involve selecting a license, assigning a few policies, and creating a user group. But in a multi-tenant setup, this process multiplies in complexity.
Without standardization, each tenant may handle provisioning differently, leading to policy misalignment, user confusion, and inefficient license use. This can result in onboarding delays, missed access requirements, and increased admin effort to manually correct inconsistencies later.
To streamline this, design a central provisioning framework that includes defined user roles, associated access levels, required licenses, and Teams configurations. Think of it as a provisioning playbook that can be applied consistently across all tenants, regardless of location or business unit.

Tip: Read our 5 Tips For Building A Robust Provisioning Plan to give you a guide on where to start.
2. Standardize and Synchronize Teams Policy Templates
Policy misalignment across tenants is one of the most common causes of inconsistent Teams experiences. Admins often find that guest access, file sharing, or app permissions vary between environments, not due to strategy, but due to lack of central oversight.
Avoid this by creating a core set of Teams policy templates for messaging, meetings, app permissions, and calling. Apply these templates across tenants either through repeatable PowerShell scripts or a centralized platform that supports policy replication.
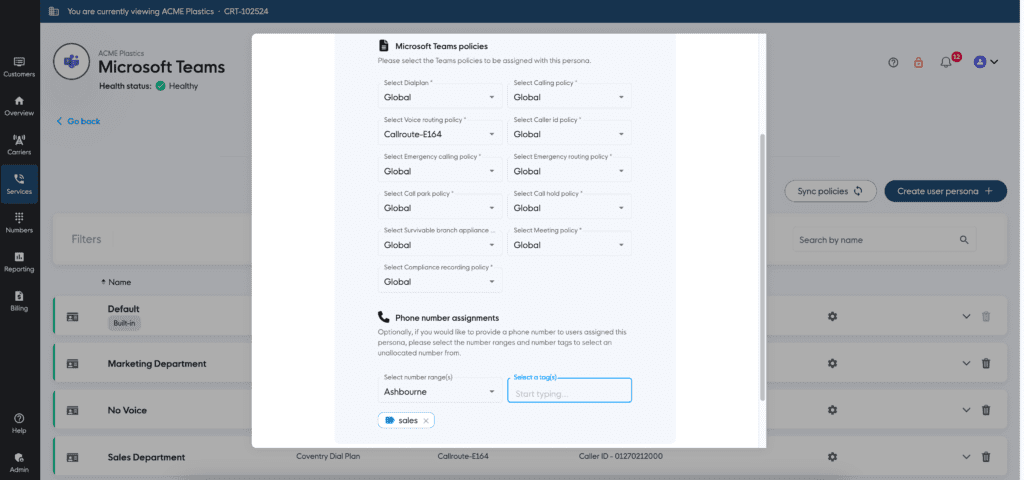
Document all changes and ensure regular audits against your baseline to detect drift. Maintaining policy uniformity improves governance, reduces risk, and helps deliver a predictable user experience within or across tenants.
Tip: start with a full list of the policies and features like this Microsoft Teams Phone Feature List.
3. Implement Role-Based Access Control (RBAC) Across Tenants
As the number of tenants and administrators grows, so does the risk of misconfiguration, accidental data exposure, or permission sprawl. Without clear delegation, IT teams may have broad admin access across environments they don’t manage, leading to inconsistent changes and reduced accountability.
To address this, apply RBAC principles at both the Microsoft 365 and Teams level. Define roles (such as global admin, regional IT, service desk, or voice engineer) and restrict their access based on business requirements.
While Microsoft allows some delegation within a tenant, a multi-tenant platform enables you to scope access by tenant, department, or role from a single interface. This ensures each admin only sees and manages what’s relevant to them, reducing risk and increasing clarity.
Tip: look for advanced granular RBAC which can apply access to specific users and numbers by EntraID attribute.
4. Automate the User Lifecycle with Joiner-Mover-Leaver Workflows
One of the biggest gaps in multi-tenant environments is user lifecycle automation. Without automated provisioning and deprovisioning, IT teams rely on manual processes, resulting in delays, access inconsistencies, and orphaned accounts.
Implement ‘Joiner-Mover-Leaver’ (JML) or ‘moves, adds, changes, and deletions’ (MACDs) automation across all tenants. When a new employee joins, they should automatically be assigned the correct licenses, policies, and Teams access. When they change roles, policies and access should update accordingly. When they leave, accounts should be disabled, licenses reclaimed, and data retention policies triggered.
Tip: Power Automate, Graph API, or identity platforms like Entra ID can help facilitate these flows. However, for multi-tenant environments, a centralized provisioning tool makes lifecycle management far more scalable and reliable.
5. Centralize Identity and Authentication Strategy
In multi-tenant environments, identity fragmentation can lead to serious user confusion, duplicated accounts, and gaps in compliance. Users may end up managing multiple logins or experience inconsistent MFA prompts and conditional access across tenants.
To improve consistency and control, centralize identity using Entra ID (formerly Azure AD). You can designate a primary identity source and use cross-tenant synchronization to securely replicate user profiles across tenants. This ensures a single source of truth for user identities, even across distinct environments.
Tip: See Microsoft’s cross-tenant identity guidance: https://learn.microsoft.com/en-us/azure/active-directory/external-identities/cross-tenant-access-overview
Enforcing global conditional access policies, MFA, and single sign-on via Entra ID will reduce support burden and strengthen security for your Teams environment at scale.
6. Enforce Naming Conventions and Directory Hygiene
Inconsistent naming of users, Teams, policies, and resources creates chaos, especially when multiplied across multiple tenants. Over time, this erodes confidence in directory accuracy and makes reporting or automation far more complex.
Define clear naming conventions for:
– User principal names (e.g. [email protected])
– Teams and channels (e.g. Region-Department-Project)
– Policies and templates (e.g. Teams Policy-Sales-EMEA)
Apply these conventions consistently using scripting or automation, and conduct regular audits to correct legacy discrepancies.
Clean directory structures improve visibility, prevent duplication, and lay the foundation for reliable automation.
7. Optimize License Assignment and Cost Management
Licensing is often one of the most expensive aspects of Microsoft 365. When operating across multiple tenants, it’s easy to lose sight of who is consuming what, and whether those licenses are even being used. Without central oversight, orphaned licenses, double assignments, and underutilized plans quickly drain budgets.
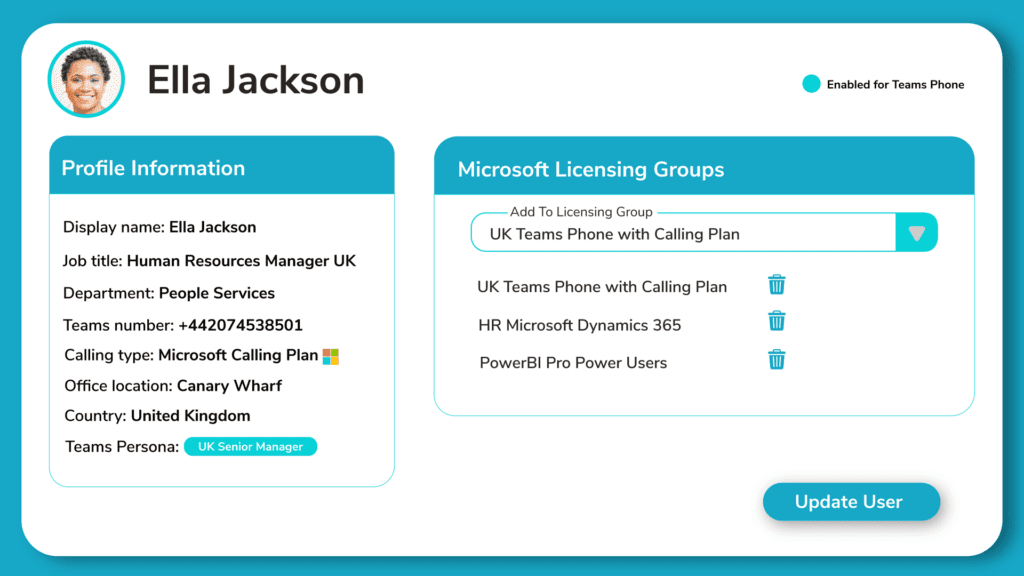
Start by implementing group-based licensing policies wherever possible. In multi-tenant setups, use reporting tools or a centralized platform that gives you tenant-wide license visibility. Set up automated workflows to reclaim licenses from inactive or offboarded users.
You should also establish regular license audits to evaluate license type usage (E1, E3, E5), validate usage patterns, and determine whether your investment aligns with user needs. This not only saves money, but it also ensures the right users have access to the right tools.
8. Centralize Monitoring and User Analytics
Monitoring Microsoft Teams usage and performance is challenging enough in a single tenant—but exponentially harder across many. When each tenant stores its own logs and metrics, it becomes nearly impossible to diagnose performance issues or understand user adoption without logging into each tenant individually, let alone gaining a holistic insight.
Centralize your reporting and analytics using Microsoft Purview (for compliance-related activity), Teams usage reports, or advanced third-party solutions that consolidate insights across environments.
Tip: Multi-tenant management platforms may also offer cross-tenant dashboards that monitor call quality, user activity, and configuration changes in one place.

With central analytics, IT teams can detect anomalies faster, spot adoption gaps, and plan change management strategies more effectively.
9. Use Guest Access Strategically
Cross-tenant collaboration is essential in many modern businesses. Yet granting every external user a full tenant account is inefficient and risky. Guest access is a built-in feature that enables secure collaboration without needing to fully provision users in every tenant.
Implement Microsoft Entra B2B guest policies across tenants and define clear access scopes. Limit guest permissions to only what’s needed (e.g., Teams membership, file access) and use expiration policies to automatically remove access after a period of inactivity.
Guest access is especially useful for project-based collaboration, external contractors, or bridging multiple business units without merging directories. When managed correctly, it reduces complexity and increases agility.
10. Consolidate and Simplify Voice Infrastructure
Direct Routing and Session Border Controllers (SBCs) are critical for enabling PSTN calling in Microsoft Teams but managing them separately in each tenant is resource intensive. Each deployment may involve separate routing tables, failover logic, and number plans, creating unnecessary duplication and configuration sprawl.
Look for solutions that support multi-tenant SBCs and centralized number management. This allows you to share a single SBC across multiple tenants, unify routing rules, and provision users faster with fewer errors.
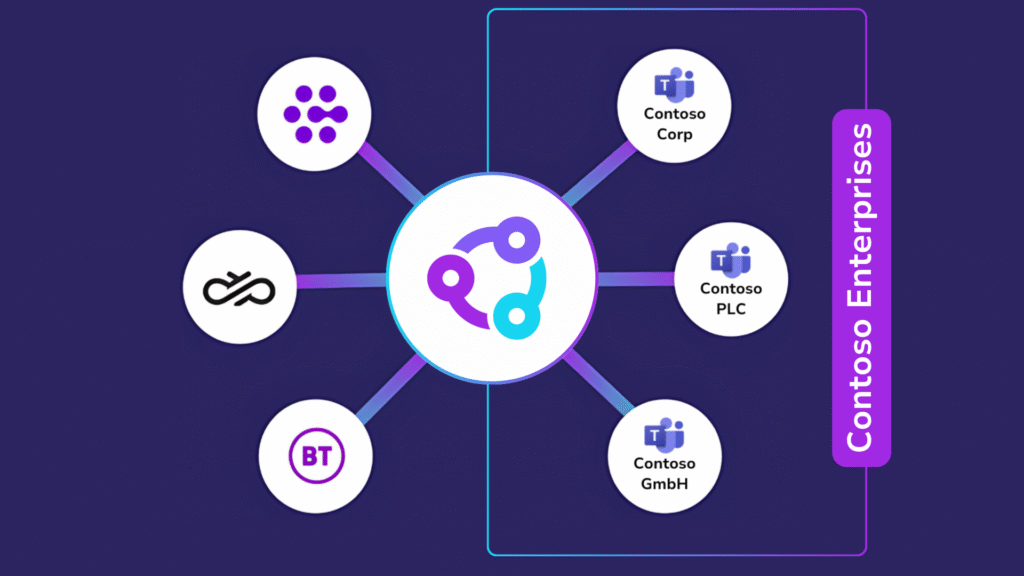
With centralized voice infrastructure, IT teams can simplify support, reduce configuration time, and provide more consistent call experiences, especially across global locations or post-M&A environments.
How Callroute Orto Simplifies Microsoft Teams Multi-Tenant User Management
Every best practice outlined in this guide, from provisioning frameworks to voice consolidation requires time, consistency, and coordination across multiple Microsoft 365 tenants. But when managed manually using siloed tools, these processes can be complex, slow, and prone to error.
Orto by Callroute is purpose-built to centralize Microsoft Teams management across unlimited tenants.
From a single interface, IT admins can:
- Provision users across tenants using reusable templates and pre-configured role types
- Apply consistent Teams policies at scale with automatic drift detection
- Automate joiner-mover-leaver workflows with full license and number lifecycle handling
- Get cross-tenant visibility into call performance, user activity, and compliance events
- Delegate access with granular RBAC, so the right teams manage only what they need
- Report and audit everything centrally with customizable dashboards and threshold alerting (or: alerts)
Whether you’re managing 3 tenants or 300, Orto replaces time-consuming manual processes with scalable automation, so your IT team can focus on strategic work. Not firefighting configuration drift or chasing down inconsistent policies.
Ready To Streamline Microsoft Teams Multi-Tenant User Management?
Book a demo or contact our team to see how Orto can work for your multi tenant environment.






