Enterprise Microsoft Teams environments rarely stay simple for long.
As tenants grow across regions, subsidiaries and business units, a small group of central admins in the Teams Admin Center (TAC) end up with access to parts of the environment they don’t directly own.
A Teams admin in London can see and change settings for New York, APAC and acquired subsidiaries, even if they only look after UK users in practice.
For IT leaders, that’s a governance problem as much as a security one.
You want local teams to handle day-to-day changes for “their” users and numbers, but you don’t want them browsing or modifying everything else in the tenant.
Granular roles-based access control (RBAC) is how you close that gap.
By keeping the familiar Microsoft Entra and TAC roles, but tightly scoping what they can actually see and manage, global enterprises can safely hand control to regional teams while central IT retains oversight, standards and accountability.
This article explains the value granular RBAC adds over standard RBAC, and why it’s critical for global enterprises that want to avoid a lot of operational, security and compliance pain further down the line.
What Is The Standard RBAC in Teams Admin Center?
Role-Based Access Control (RBAC) is implemented through predefined Microsoft Entra roles such as:
- Teams Administrator
- Teams Communications Administrator
- Teams Device Administrator
- Teams Communications Support Engineer, and others
These roles are assigned in Entra ID and then surface in the TAC to control who can:
- Manage users and policies
- Configure voice and calling settings
- Administer devices and meeting settings
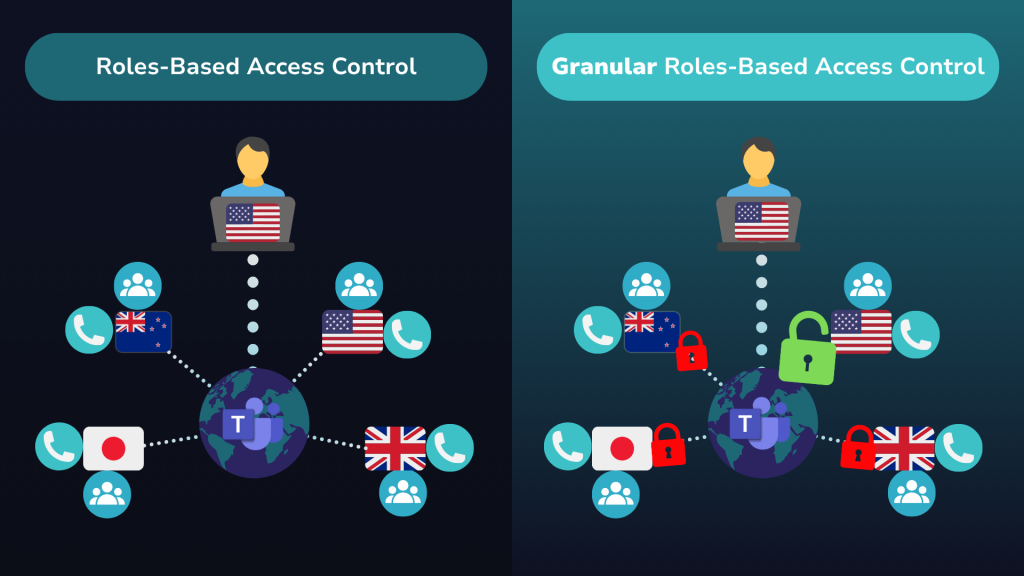
In practice, that means a single Teams Administrator can search for and change settings for every user and phone number in the tenant, even if they only look after one region or business unit in reality.
RBAC applies the same role across the whole tenant. So an admin for Germany can still see and modify users, numbers and policies for North America or APAC, unless you add extra controls on top.
RBAC simplifies access management: you assign a role, and that admin gains a broad set of permissions across the tenant.
For smaller or simpler environments, this is often enough. However, there are some clear limitations when Teams is used at scale as access is typically tenant-wide, even if that person is only responsible for one region, department, or business unit.
In other words, RBAC in TAC gives you a good baseline – but it’s still a broad-brush model in environments that increasingly need precise, “granular and targeted” control, where admins need to be restricted to a specific set of users or phone number ranges.
What Is Granular Roles-Based Access Control with Orto for Teams?
You still use your existing Microsoft Entra / TAC roles (e.g. Teams Administrator, Teams Communications Administrator). What Orto adds is the ability to limit the reach of the tenant-wide permissions through these roles to specific parts of your environment (users and/or phone numbers).
See Granular Roles-Based Access Control in action
If you’d rather see this in action, this short demo shows how a Teams Administrator account is narrowed down from tenant-wide access to just the users and phone numbers they’re responsible for. You’ll see Orto Security Groups and rules based on Entra ID attributes and Microsoft 365 groups automatically limit what that admin can view and change, so they can support their region without touching the rest of your tenant.
In Orto, that looks like this:
- A service user in the 365 tenant is used to connect Orto to the target 365 tenant. The service user roles/permissions (Teams Admin etc.) in 365 define what this user can change. Callroute uses the service to admin the target tenant (act on behalf of).
- You define Orto Security Groups that represent the slices of your environment you want to control – for example UK, DACH, Retail Stores, or Enterprise Sales.
- You use rules based on Entra ID attributes (like country, department, office) and/or Microsoft 365 group membership to automatically place users into the right Orto Security Groups.
- You associate phone numbers with those same Security Groups.
- Assign Callroute admins permissions to be associated with Orto Security Groups.
- Now when a Callroute user logs in, they only see the users and phone numbers they are allowed to manage in the connected 365 tenant.
So, a “Teams Administrator” in Orto might only see and manage:
- Users in the UK group
- Numbers associated with the UK region
while another Teams Administrator using only Teams Admin Centre has access to, say, North America or Retail Stores.
That’s the granular part – Orto lets you keep Microsoft’s RBAC roles, but apply them only to the regions, sites, departments, groups, and number ranges they should control.
Further reading: If you’d like a deeper, step-by-step explanation of how the model works, including more examples by region, site and business unit, our article “What Is Granular Roles-Based Access Control?” (https://callroute.com/orto-for-teams/what-is-granular-roles-based-access-control/) walks through the concept in more detail.
How Granular Roles-Based Access Control Changes The Game
When you rely on standard RBAC in the Teams Admin Center alone, a small number of high-privilege roles often end up with very broad access. Even with well-run processes, those admins can typically see and change far more than they need to – especially in global or multi-tenant environments.
Granular RBAC with Orto changes this by limiting the reach of existing Entra / TAC roles to the right parts of your environment. Instead of every Teams Administrator having tenant-wide visibility and control, Orto Security Groups and Entra-driven rules define exactly which users and phone numbers each admin can manage.
This delivers several practical advantages:
Stronger security
High-privilege roles are no longer tenant-wide by default. Teams admins only see and change the users and numbers in their assigned Security Groups, reducing the blast radius of mistakes or misuse.
Cleaner compliance and audit
Because access is tied to clear scopes (such as region, site, or business unit) and driven by Entra attributes and Microsoft 365 groups, it’s easier to evidence who can change what, and where. This is especially important in regulated or multi-region organizations.
Faster operations without losing control
Local or regional admins can handle day-to-day tasks for their own users and number ranges, rather than everything being routed through a small central TAC team. Central IT still defines the roles, rules, and overall configuration in Orto.
Standardized policies with local assignment
With Orto, central IT can define policy packs (Personas) – standard combinations of Teams and voice policies – and then devolve the rights to assign those Personas to local admins. Regional teams can quickly assign the correct Persona to their users, but they cannot create their own ad-hoc mix of policies.
This keeps policy configuration consistent, prevents incorrect or incomplete policy sets being applied, and stops regional admins from “going rogue” with their own combinations.
Governance at scale
You keep Microsoft’s RBAC model but gain a governance layer that scales with your organization. As users move role, region, or department, Orto’s rules automatically adjust which admins can manage them based on Entra attributes and group membership.
Put simply: RBAC in TAC defines what an admin can do. Orto’s granular RBAC defines which users and phone numbers they are allowed to do it for – and which standardized policy packs they are allowed to assign.
| Aspect | RBAC in Microsoft Teams Admin Center (TAC) | Granular RBAC with Callroute’s Orto for Teams |
|---|---|---|
| Role model | Uses predefined Microsoft Entra / TAC admin roles (e.g. Teams Admin, Comms Admin) | Uses the same Entra / TAC admin roles |
| Scope of access | Roles are typically tenant-wide, with limited scoping via Administrative Units | Orto limits the ability to administer on certain users and phone numbers via Orto Security Groups (e.g. region, site, department, business unit) |
| Precision | Broad – admins can see and change users that are beyond their remit | Granular – admins only see and manage users and numbers within their assigned Orto Security Groups |
| Policy management | Policies typically configured and combined manually by central admins | Central IT defines standard policy packs (Personas); local admins can assign them but cannot change the underlying combinations |
| Governance & Operations | Central TAC admins handle many day-to-day changes across the whole tenant | Local/regional admins handle their own areas; central IT defines roles, rules and guardrails in Orto |
Roles-Based Access Control vs Granular Roles-Based Access Control: FAQs
Is granular RBAC replacing Microsoft’s built-in RBAC in Entra and the Teams Admin Center?
No. Orto for Teams uses your existing Microsoft Entra and TAC roles, such as Teams Administrator or Teams Communications Administrator.
Granular RBAC adds a governance layer on top, limiting what those roles can see and change to the parts of the environment they actually manage – for example a specific region, set of sites or number ranges.
Why isn’t standard Microsoft Teams RBAC enough for global enterprises?
Standard RBAC in Entra and TAC works well in smaller or simpler environments, but in a large tenant it typically gives a small group of admins tenant-wide visibility and control.
That means a local IT admin for one country can often see and modify users and numbers in every other country as well. It makes delegation easier, but it also makes it harder to enforce least-privilege access and prove to auditors that people only have the permissions they genuinely need.
How is Granular RBAC different from using administrative units or simple role scoping?
Administrative units and similar features offer some scoping, but they usually don’t match how the business is really organised or how voice is carved up.
With Orto, Security Groups and rules based on Entra ID attributes and Microsoft 365 groups let you align admin access with the way your organisation actually works – for example “UK Sales”, “DACH Customer Support” or “Retail Stores” – and link those scopes directly to the relevant number ranges.
Will Granular RBAC make things harder for my central TAC team?
No. Central IT still owns the guardrails. Your existing Microsoft Entra and Teams Admin Center roles stay as they are, and Orto simply connects to the tenant using a service account with those permissions.
In Orto, central IT defines the Security Groups, the rules that place users and numbers into those groups, and any standard policy packs (Personas) they want local teams to use.
Granular RBAC doesn’t change how you configure Teams itself – it changes who can see and manage which users and numbers through Orto.
Central IT keeps control of the overall model and configuration, while local and regional admins handle day-to-day changes for the users and number ranges in their own area.
Does Granular RBAC help with compliance and audit?
Yes. Because access is tied to clear scopes such as region, site or business unit and driven automatically by Entra ID attributes and group membership, it becomes much easier to evidence who can change what, and where.
When an auditor asks “who can change calling settings for users in France?”, you can answer with a specific list of admins scoped to that country, rather than everyone with a tenant-wide Teams Administrator role. With Orto, you also have a full audit log available within the portal so you can view who made changes and when.
The Smarter Way to Secure Microsoft Teams
For most organizations, RBAC in the Teams Admin Center is the starting point. Microsoft Entra roles and TAC give you a solid, standard way to control what your Teams admins can do.
The challenge is where those roles apply.
In large tenants, admin roles are often too broad. You need a way to keep using Microsoft’s RBAC model but apply it in a way that matches how your business is structured and how your environment is segmented (by region, department, etc.). That’s where Callroute’s Orto for Teams comes in.
Orto doesn’t replace TAC or Entra roles – it limits the reach of those admins to specific numbers and users. Using Orto Security Groups and rules based on Entra ID attributes and Microsoft 365 groups, you can:
- Limit high-privilege roles to specific regions, sites, departments, or business units
- Ensure admins only see and manage the users and phone numbers within their scope
- Delegate day-to-day work safely to local IT, while central IT keeps governance and visibility
You keep the familiar Microsoft RBAC model – and layer on the granular control and automation that complex Teams environments demand.
Discover how Orto adds granular control to help you manage Microsoft Teams securely and efficiently.
Book a demo to see how it could work for your enterprise!






